zkSecurity is helping zkHack kick off a new season of zkHack whiteboard sessions!
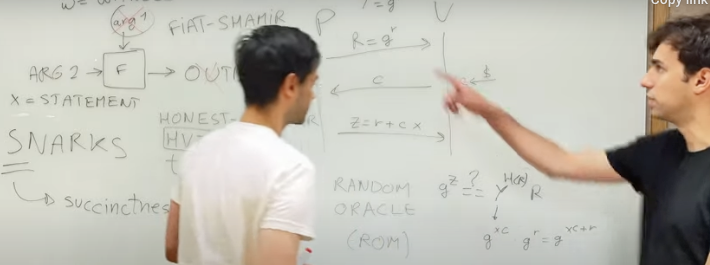
In this module, Nicolas Mohnblatt and David Wong from zkSecurity dig into the term “Zero Knowledge” and discuss what this property actually is, when it is being used (or not) and what characteristics some systems need in order to be considered truly ZK. They then highlight the different types of ZK — perfect, statistical, and computational –, discuss the distinction between dishonest and honest verifiers, and the preference for adaptive models over non-adaptive ones. Additionally, they explore methods for generating hiding commitments from techniques such as KZG, Pedersen, and hashes, and conclude with an overview of the zero-knowledge analysis of PLONK.
watch it on youtube or on the zkhack.dev page
What’s in it? Check the timestamps:
00:00 – Introduction 01:03 – ZK, SNARKs, Proving… High-level overview 04:53 – Defining ZK and the concept of Simulator 08:41 – A concrete example of a Simulator with the Schnorr Identity Protocol 14:06 – Honest vs. dishonest Verifier 19:28 – Non-interactive to interactive protocol with Fiat-Shamir 24:50 – The 3 flavors of ZK 29:52 – Application to the PLONK protocol 46:37 – Managing KZG and its trusted setup 50:00 – The ZK flavor of PLONK 57:02 – Summary